
Prof. Dr. Alexander Schinner
Showhacking
In an increasingly networked and digitalized world, security vulnerabilities and threats to companies are omnipresent. While the rapid development of technologies brings many benefits, it also opens new gateways for cyberattacks and data loss. Maintaining a robust security infrastructure is a challenge that every company must face.
We support you with a team of experienced experts in preventing and defending against cyber attacks and information security incidents by demonstrating how hackers think and act.
The basic idea of Security Awareness Showhacking is to immerse the audience in the mind of a hacker and show how the employees of the virtual company Compor AG can be misled into making mistakes. The aim is for viewers to understand how attackers operate so that they can also recognize and see through these behaviours in everyday life. In this way, a much more profound change in behavior towards security is initiated than is possible through purely web-based training or slide presentations.
Presentations on a wide variety of topics can be offered as part of a security awareness show hacking event. These can, for example, be compiled individually according to customer requirements on social engineering, technical vulnerabilities, information leakage, hacker tools, or reports on contacts with real fraudsters.
We offer flexibility in topic selection and adaptation to the technical knowledge of the audience, ensuring inclusivity. Whether your audience is technically experienced or non-IT-savvy, we can tailor the showhacking to suit their needs. The event can be held in person, hybrid, or via video stream, providing you with the choice that best fits your requirements.
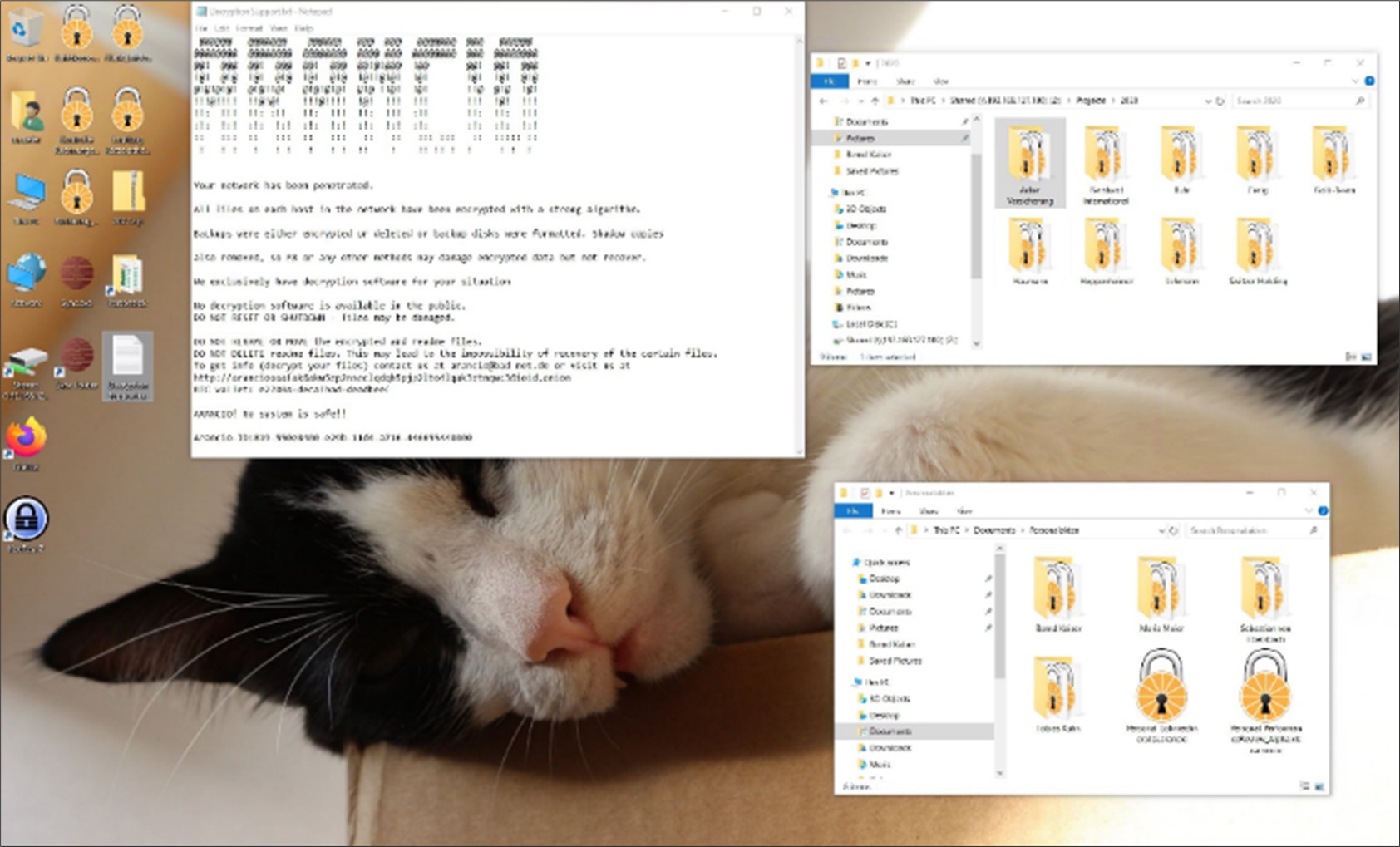
We offer you a wide range of different modules. These include, among others:
Do you have any questions or want more information about our offers? Please write to us! We will happily advise you on our services and work with you to find the right solution for your request.

Prof. Dr. Alexander Schinner