
Philipp Zimmermann
Cyber-Risikomanagement
In an era of pervasive and escalating cyber threats, it is imperative to adopt a proactive approach to safeguarding your organisation against potential risks.
BDO Cyber Security is your trusted partner, providing comprehensive cyber security solutions and specialised services in the domains of information security management (ISMS) and cyber risk management.
With our expertise, you can assess risks, address vulnerabilities and implement effective preventive measures to ensure resilience against cyber-attacks.
Let us collaborate to enhance the security of your company and personal data, and to preserve the integrity of your system
Cyber risk management is a core element of the information security management system (ISMS). It focuses on the identification, assessment and treatment of risks in cyberspace.
Our services are designed to assist you in achieving your desired cyber risk management objectives:
Please refer to the "Methodology" section for further information.
Implementing effective cyber risk management can help to:
In addition, a functioning risk management system will help you to meet the requirements of ISO 27001, BSI IT-Grundschutz and GDPR as well as industry-specific laws and regulations such as DORA and NIS2.
It addresses not only IT-based attacks, but also other potential risks in the context of information security, such as data breaches, system failures or insider threats.
The cyber risk management cycle encompasses the identification, assessment, treatment, communication and monitoring of risks to information systems in the context of cyber security.
The BDO Cyber Risk Management Cycle assists organisations in safeguarding their information systems against cyber-attacks and other digital and physical threats. The cycle comprises the following steps:
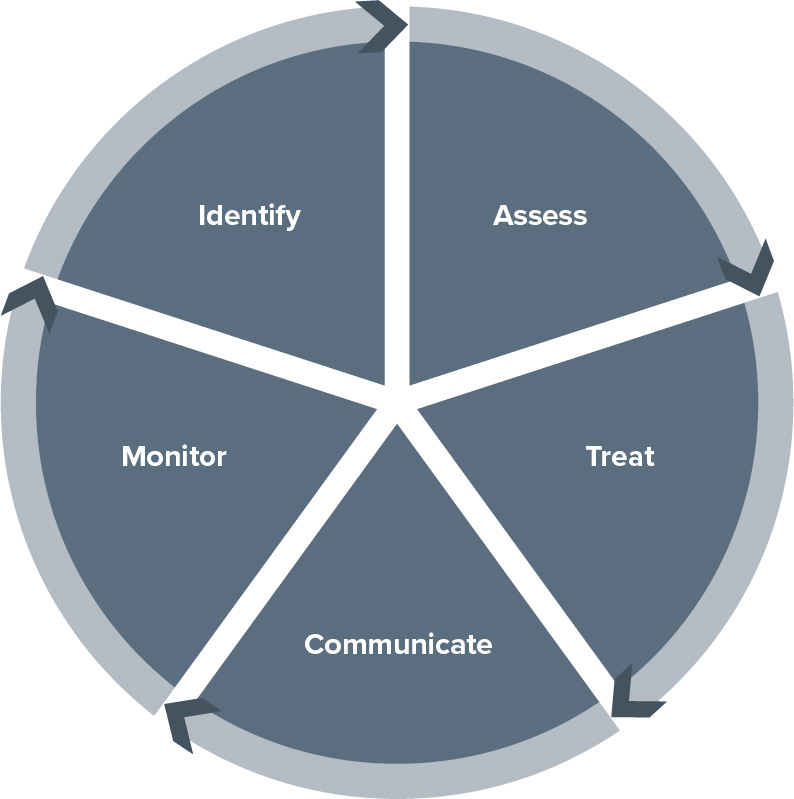
Systematic risk identification provides a transparent overview of your cyber security situation and enables you to take targeted measures to mitigate risks.
The risk assessment process enables you to concentrate your resources on the most significant cyber risks and prioritise your security measures.
Risk transfer: This involves the transfer of risk to other parties. This can be achieved through insurance or by outsourcing the risky task to an external service provider. It is important to ensure that contracts are properly designed to cover all eventualities.
Risk acceptance: The risk is accepted. This can be an effective means if risk treatment costs are no longer economically viable or if the hazard could only lead to damage under extremely specific conditions. Alternatively, this may be due to the fact that no sufficiently effective countermeasures are known or can be implemented.
Risk acceptance: The risk is accepted. This can be an effective means if risk treatment costs are no longer economically viable or if the hazard could only lead to damage under extremely specific conditions. Alternatively, this may be due to the fact that no sufficiently effective countermeasures are known or can be implemented.
Implementing effective risk management strategies can safeguard your company against cyber threats in the long term and mitigate the consequences of any potential incidents.
Open risk communication is integral to establishing transparency, trust and a shared understanding of cyber security within your company.
Implementing continuous monitoring and review processes is the most effective way to ensure that your cyber risk management is always up to date and that your security measures are optimally effective.
BDO Cyber Security has many years of experience and in-depth expertise in the field of cyber security. Our team of specialists provides comprehensive support to businesses and industries of all sizes, helping them to enhance their cyber resilience and protect themselves effectively against cyber threats. We offer a wide range of cyber risk management services, including:
Our holistic approach and cross-industry expertise make us a reliable partner for your business. We work closely with you to develop customised solutions that are perfectly tailored to your individual requirements.
With BDO Cyber at your side, you benefit from our many years of experience, our in-depth specialist knowledge and our innovative solutions. We provide comprehensive support in enhancing your cyber resilience and optimally safeguarding your company against cyber threats.

Philipp Zimmermann