Philipp Zimmermann
NIS-2 Service
For SMEs, the risk of cyber attacks is higher than ever before and continues to increase. It can be assumed that your company will also be affected sooner or later. Professionally managed SMEs have been working intensively on protecting their data and systems for some time now, and the legislator is now also demanding this. The NIS-2 Implementation Act (NIS = Network & Information Security) transposes an EU directive into national law and is therefore also expected to become mandatory for many German SMEs from March 2025.
Our cyber security experts help you to proactively strike a balance between vulnerability detection and defence, corporate protection and NIS 2 compliance. This is done by individually weighing up the risks and costs so that you can continue to focus on your core business.
It is up to the companies themselves to determine whether they are affected by the NIS 2 Directive. According to estimates, around 30,000 companies in Germany alone could be affected by this directive. The directive leads to stricter reporting obligations and clearly defined sanctions in the event of non-compliance. This emphasises the need for proactive security strategies.
The scope of the NIS 2 Directive extends far beyond the previously recognised key critical infrastructure companies (KRITIS). Categorisation as an affected company is based on the area of activity. Company size and annual turnover also play an important role. This means that a large number of small and medium-sized companies will also be included in the obligations of the directive in future.
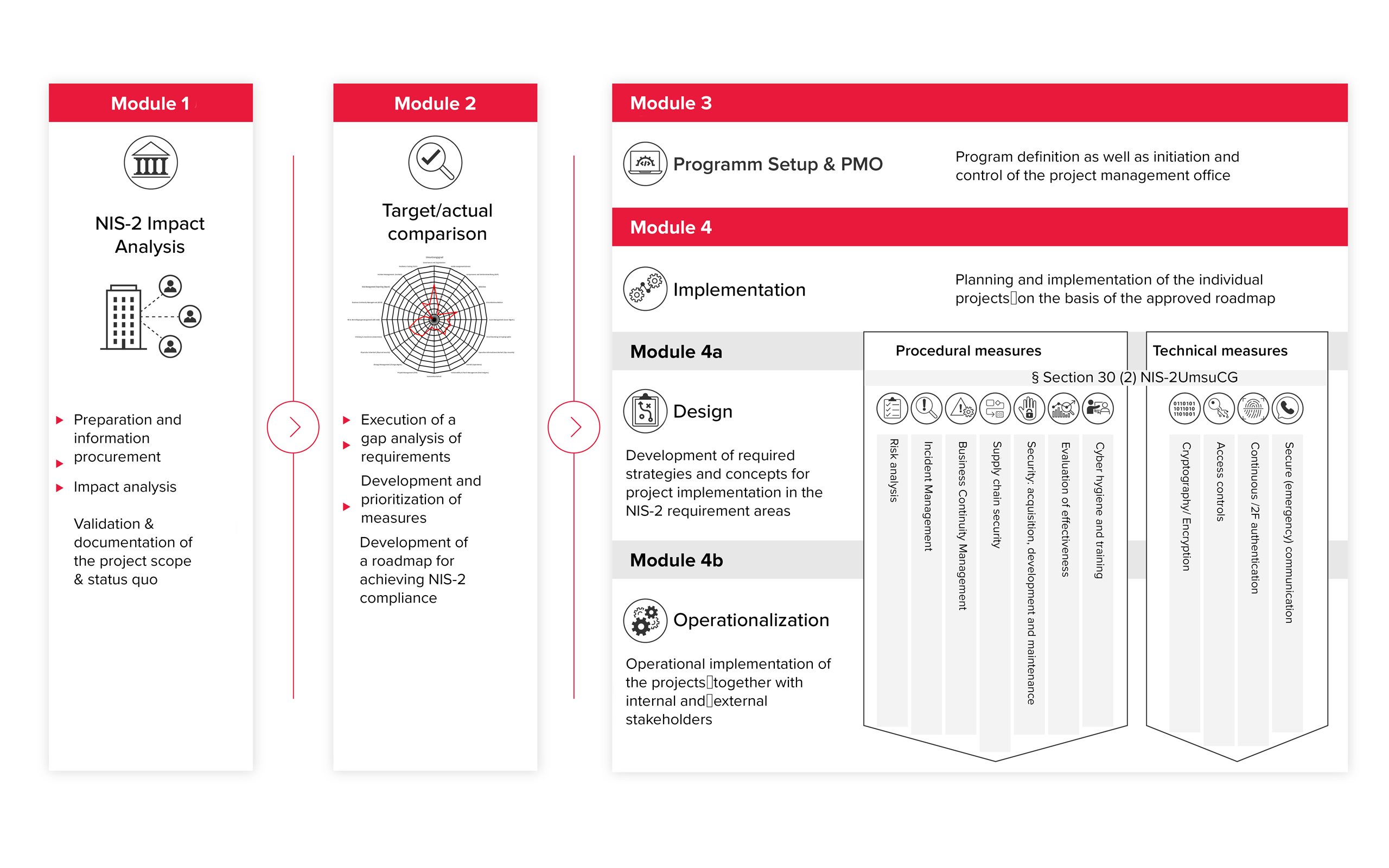
Our BDO NIS-2 Readiness approach to achieving NIS-2 compliance consists of a total of four phases:
During the documentation check, existing documentation and diagrams (e.g. network structure plans) are reviewed and their content checked against the requirements.
On-site analysis
As part of the on-site analysis, the relevant processes and important objects are examined and analysed during site visits and interviews with the responsible persons
As part of the GAP analysis, we assess the maturity level of your company in relation to the implementation of the NIS 2 Directive with regard to the following topics and measures:
Complex of measures | Technical measures | Procedural measures |
| Management & Policies |
| |
| Personal Security |
|
|
| Physical security |
|
|
| Supply Chain |
| |
| IT Security & Networks |
|
|
| Business Continuity |
|
|
| Incident Management |
|
|
The implementation of your NIS-2 compliance takes place through careful planning and realisation based on the previously approved roadmap.
The implementation can be divided into the following phases:
We would be happy to support you in implementing the identified technical and procedural measures with the help of our other BDO Cyber Services: