
Dr. Antje Winkler
Red Teaming
Every company’s IT environment and security measures are unique. Therefore, attackers need to adapt accordingly, tailoring their cyber attacks to fit each specific organization. Potential attacks might include targeted phishing attempts to obtain a user’s login credentials or exploiting vulnerabilities in publicly accessible services. Once an attacker gains initial access, they will further explore and traverse the company's network.
We offer various scenarios that reflect real-world attacker tactics. Each scenario sets the starting point for the campaign and outlines the methods the simulated attacker will use to infiltrate your corporate network:

This scenario assumes that an attacker has already gained access to internal IT systems or that an internal perpetrator is misusing their existing access. To simulate this scenario, you provide us with an internal point of access. Based on this, our Red Team will assess how such an attacker could expand their access rights and compromise further systems.
Examples:

We act like an attacker who tries to bypass the physical perimeter protection through targeted deception and install a prepared device on the company’s premises. The goal is to overcome on-site security measures and covertly gain access to the company network (e.g., by planting a mini-PC).
Examples:

With this approach, we take on the role of an attacker conducting cyber attacks over the internet. Using various information gathering techniques, we identify vulnerabilities in the external perimeter and attempt to exploit them to infiltrate the corporate network.
Examples:

Before commencing the campaign, we will analyze relevant threat scenarios in a joint kick-off meeting, define appropriate scenarios, and determine the attack targets. This information is then documented in the Rules of Engagement, which the campaign is based on.
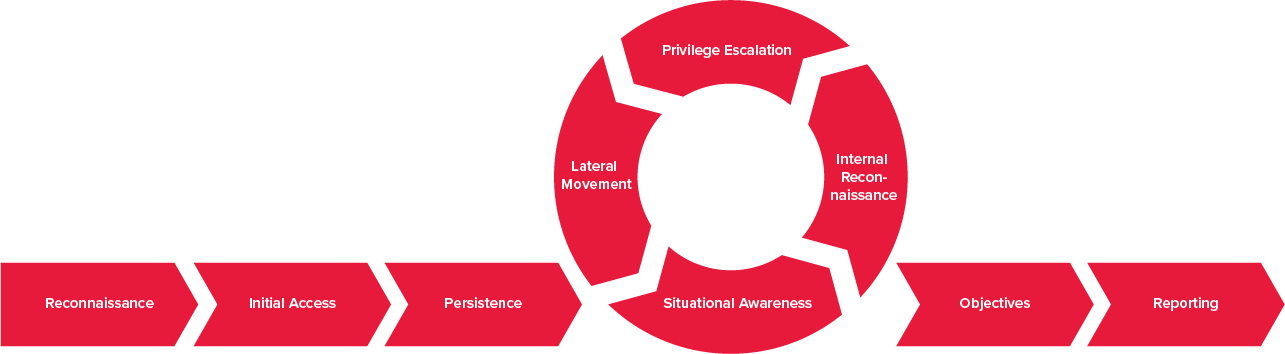
The attack simulation in a Red Teaming campaign unfolds through nine, partly iterative stages:
In a Red Teaming campaign, the following roles are defined:
The phases of the Red Teaming campaign are defined as follows:

During the reconnaissance phase, information about the company is gathered. This information is obtained from publicly available sources through Open-Source Intelligence (OSINT) techniques.
The aim is to obtain a picture of the situation and identify possible attack paths, which are essential for subsequent phases of the Red Teaming campaign.

The post-exploitation phase is the core phase of the campaign and includes several recurring steps:

The achievement of the campaign’s objectives is demonstrated to the White Team through jointly defined actions, such as:

Upon completion of the attack simulation, a report is provided, which includes the following:

In the final debriefing, the identified vulnerabilities and recommended actions are discussed with the Blue Team and responsible IT personnel. Any outstanding questions are addressed.
Even after the Red Teaming campaign concludes, we remain your point of contact and are available to answer any questions you may have.
There are many established methodologies and frameworks that guide a Red Teaming campaign, ensuring that the results are consistent and compliant with regulations such as the Digital Operational Resilience Act (DORA) or NIS-2.

Dr. Antje Winkler
Social Engineering
Social engineering focuses on exploiting human factors, aiming to entice employees in their respective roles to disclose sensitive information or to carry out certain actions. Starting from a successful compromise, the objective is to infiltrate the company’s infrastructure.
In addition to email phishing, alternative communication channels such as messaging services or social media are possible.
Example: